Exploring AES Modes for Robust Java Encryption
The evolution of data encryption in Java is marked by the implementation of Advanced Encryption Standard (AES) mechanisms, which are quintessential for securing sensitive information.
This exploration delves into the various AES modes, offering a nuanced understanding of their applications, strengths, and weaknesses. Unravel the intricate dance of bits and bytes that form the bedrock of data security in the Java programming landscape.
The Genesis of Encryption and Modern Progression
From the initiation of cryptographic systems, the advent of AES in the domain of Java has been revolutionary. AES, a derivative of the “Rijndael” cipher developed by Belgian cryptographers, became globally acknowledged after its endorsement by the U.S. National Institute of Standards and Technology (NIST) in 2001. This symmetric key algorithm underscores the cornerstone of contemporary cryptographic systems.
AES Unleashed in Java
In the Java ecosystem, AES operates as a block cipher with a capacity to accommodate key sizes of 128, 192, or 256 bits, catering to a spectrum of security requirements. It encrypts information in 128-bit blocks, necessitating padding mechanisms if the dataset is lacking in volume. The Java Cryptography Architecture (JCA), embedded within the Java Development Kit (JDK), facilitates the seamless execution of AES.
Parameters for Java AES Operations
AES encryption in Java demands three pivotal elements:
- Input Data: This encapsulates varied data forms, encompassing strings, files, or objects;
- Encryption Key: It can be autonomously generated or extrapolated from user-established passwords, leveraging Java’s SecureRandom and KeyGenerator classes;
- Initialization Vector (IV): The SecureRandom class is instrumental in crafting a pseudo-random IV, integral for enhanced security.
Dissecting AES Modes in Java
Java’s implementation of AES features six distinct modes, each addressing unique security and operational challenges. These include:
- ECB (Electronic Code Book);
- CBC (Cipher Block Chaining);
- CFB (Cipher Feedback);
- OFB (Output Feedback);
- CTR (Counter);
- GCM (Galois/Counter Mode).
Electronic Code Book (ECB) Examined
ECB, although straightforward, exhibits vulnerability due to its deterministic encryption of identical plaintext blocks into identical ciphertext equivalents. It finds utility in scenarios demanding the encryption of datasets beneath 128 bits, and padding mechanisms fill in for data inadequacies.
Implementing AES-ECB in Java
Java’s offering of the ECB mode is both accessible and intricate. Key generation and cipher creation are accomplished via the KeyGenerator and Cipher classes, respectively. Data encryption and decryption processes are initialized, executed, and refined, ensuring that the conversion between plaintext and ciphertext is both efficient and secure.
Java’s embrace of AES, encapsulating the elegance of varied modes and the potency of enhanced security protocols, underscores the language’s resilience and adaptability. In a world where data is as vulnerable as it is valuable, mastering the art and science of AES encryption within Java’s rich ecosystem is not just an asset – it’s a necessity.
Each AES mode, marked by its unique characteristics, addresses distinct challenges in the encryption landscape. Understanding the nuances of ECB, CBC, CFB, OFB, CTR, and GCM ensures that developers are equipped with a versatile toolkit to safeguard information. In this dynamic digital age, the mastery of Java AES encryption is tantamount to possessing the keys to an unbreachable fortress, where data remains both accessible and secure.
Cipher Block Chaining (CBC) Unraveled
Cipher Block Chaining (CBC) mode stands as a more secure alternative to ECB, incorporating intricate encryption methodologies that enhance security. In CBC, every block of plaintext undergoes an XOR operation with the preceding ciphertext block before encryption, ensuring that each encrypted block is dependent on all preceding plaintext blocks. This interdependence augments the security of the encrypted information.
- For the inaugural block, which lacks a preceding ciphertext counterpart, a 128-bit random Initialization Vector (IV) is employed. The utilization of a random IV is fundamental in augmenting the security of CBC, as it ensures that identical plaintext encrypted with the same key yields different ciphertexts, eliminating patterns and predictability;
- In practical applications, especially in the realm of AES implementations within the Java environment, the IV is often affixed at the commencement of the cipher message. This practice enhances the security and integrity of the encrypted information during transmission.
Consider the following refined Java snippet that exemplifies CBC mode encryption and decryption:
private static final String SECRET_KEY = “aesEncryptionKey”; private static final String INIT_VECTOR = “encryptionIntVec”; public static String encrypt(String value) { try { IvParameterSpec ivSpec = new IvParameterSpec(INIT_VECTOR.getBytes(“UTF-8”)); SecretKeySpec skeySpec = new SecretKeySpec(SECRET_KEY.getBytes(“UTF-8”), “AES”); Cipher cipher = Cipher.getInstance(“AES/CBC/PKCS5PADDING”); cipher.init(Cipher.ENCRYPT_MODE, skeySpec, ivSpec); byte[] encryptedValue = cipher.doFinal(value.getBytes()); return Base64.getEncoder().encodeToString(encryptedValue); } catch (Exception e) { e.printStackTrace(); } return null; } public static String decrypt(String encryptedValue) { try { IvParameterSpec ivSpec = new IvParameterSpec(INIT_VECTOR.getBytes(“UTF-8”)); SecretKeySpec skeySpec = new SecretKeySpec(SECRET_KEY.getBytes(“UTF-8”), “AES”); Cipher cipher = Cipher.getInstance(“AES/CBC/PKCS5PADDING”); cipher.init(Cipher.DECRYPT_MODE, skeySpec, ivSpec); byte[] originalValue = cipher.doFinal(Base64.getDecoder().decode(encryptedValue)); return new String(originalValue); } catch (Exception e) { e.printStackTrace(); } return null; }
Counter Mode (CTR) Explored
CTR, or Counter Mode, stands as another esteemed encryption method in the Java security architecture, renowned for its efficiency and robustness. Unlike its CBC and ECB counterparts, CTR transitions the block cipher into a stream cipher, eliminating the necessity for padding. Each block is assigned a counter value, commencing from zero, ensuring every block is uniquely identified.
- CTR’s distinction lies in its ability to perform encryption tasks in parallel, a feature that drastically enhances processing speed. Each block’s encryption is contingent on the IV and counter value, ensuring heightened security and eliminating inter-block dependencies that could potentially compromise the integrity of the encrypted information;
- It’s imperative to emphasize the cardinal rule in CTR mode – the IV should never be reused with the identical key. Such an occurrence could lead to the exposure of the key, rendering the encrypted information vulnerable to unauthorized access and compromising data security;
- A concrete Java implementation of the CTR mode underscores its effectiveness and robustness. It stands as a testament to Java’s versatile and dynamic approach to data security, ensuring that sensitive information remains impervious to unauthorized access, manipulation, or compromise;
- The integrity of encrypted information is not just about the algorithms but also about their implementation. As technology evolves, so does the complexity of securing digital assets. Java’s comprehensive suite of AES encryption methodologies ensures that developers and security professionals alike are equipped with the tools, resources, and knowledge to counteract emerging security threats and vulnerabilities.
CBC and CTR modes, with their unique characteristics, offer insights into the multifaceted landscape of data security. These encryption methods epitomize the dynamism and adaptability of Java, ensuring that as the digital space evolves, the sanctity of sensitive information remains inviolable.
Galois/Counter Mode Explored
Galois/Counter Mode (GCM) ascends in the hierarchy of AES encryption modes, esteemed for its authenticated encryption capabilities. This mode doesn’t merely focus on the confidentiality of information but extends its prowess to ensuring the authenticity of the encrypted data. It intertwines encryption and authentication, weaving a robust security fabric that is impervious to common security threats.
- A step beyond the conventional Counter (CTR) mode, GCM introduces a 128-bit authentication tag calculated concurrently with data encryption. This tag, typically appended to the ciphertext, serves as a beacon of data integrity during decryption, verifying the authenticity of the retrieved information;
- One of GCM’s distinguished features is its capacity to authenticate additional unencrypted information accompanying the plaintext. In the intricate dance of data security, ensuring the integrity of associated metadata is paramount. GCM meticulously verifies the authenticity of such data, thwarting attempts to manipulate or corrupt the associated encrypted information.
In a realm where data integrity and confidentiality are paramount, GCM emerges as a sentinel of security. It not only encrypts data but also fortifies it with an authentication mechanism, making it a favored choice among security professionals and developers alike.
Cipher Feedback and Output Feedback Modes Demystified
In the vast landscape of AES encryption modalities, Cipher Feedback (CFB) and Output Feedback (OFB) modes carve their distinct niches. These modes transmute the block cipher into a stream cipher, introducing nuanced encryption dynamics that enhance data security.
CFB commences with the encryption of the Initialization Vector (IV), subsequently performing a XOR operation with plaintext blocks to yield the ciphertext. However, its inability to parallelize encryption processes necessitates the padding of data, a characteristic that distinctly separates it from OFB.
OFB, conversely, escapes the requirement for padding, attributed to its inherent design that facilitates parallel encryption processes. It shares a foundational similarity with CFB in the initial steps of encryption but diverges in execution, offering an alternative that is as secure as it is efficient.
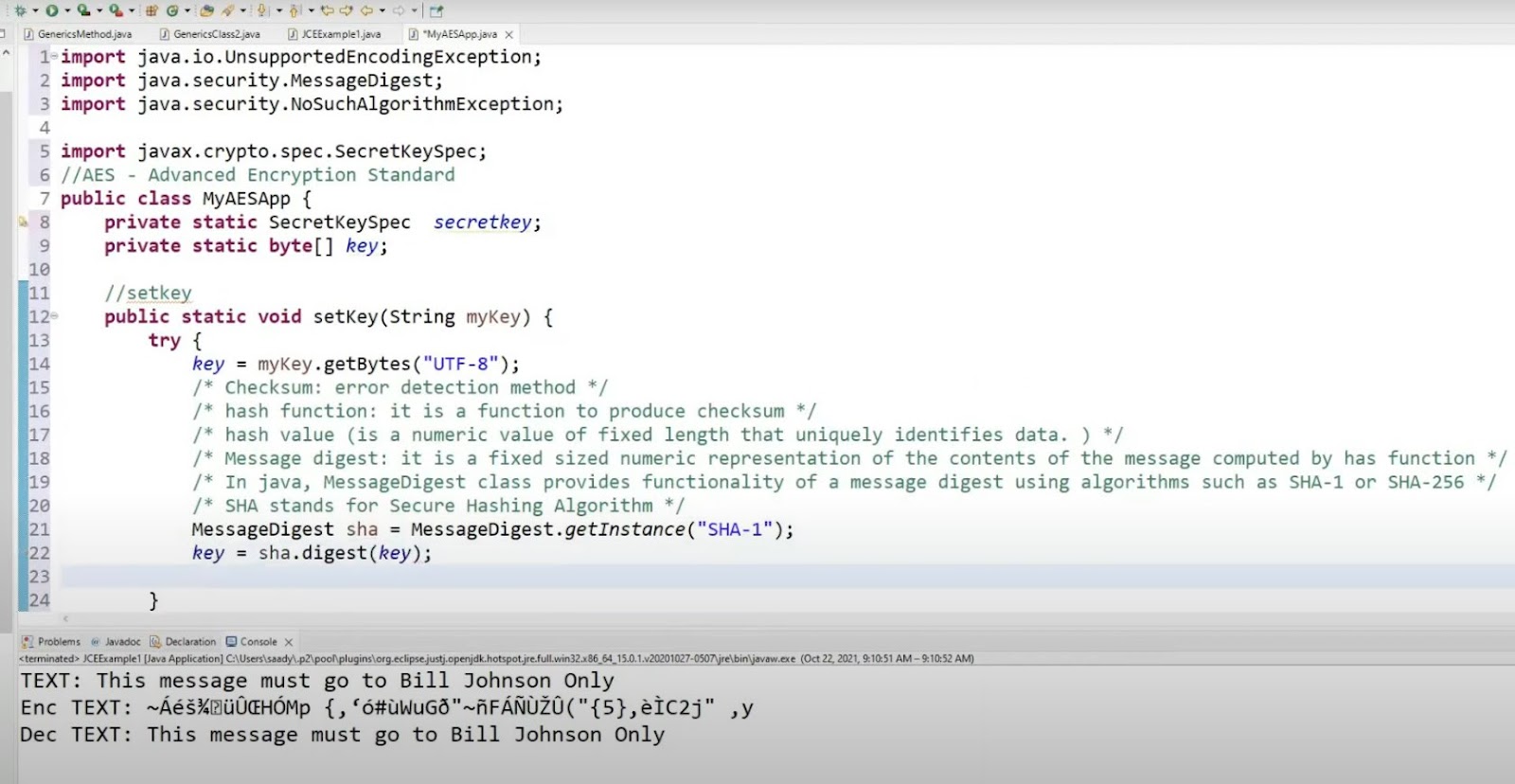
Delving into Java AES Password-Based Encryption and Decryption
In the intricate realm of encryption, the generation of random keys is a well-trodden path. However, the narrative takes a nuanced turn when the focus shifts to password-based encryption. Herein, RFC 8018 shines a light on the pathway, elucidating the Password-Based Cryptography Specification (PKCS) that meticulously crafts encryption keys from user-provided passwords.
The allure of password-based encryption lies in the augmented security it bestows. A password, chosen by the data’s custodian, injects a personalized security layer, intertwining human memory and computational encryption to create an impervious security barrier.
To navigate the intricate corridors of password-based encryption, PKCS demands three cardinal inputs:
- Password: Bestowed by the data custodian, it’s the cornerstone of personalized encryption;
- Salt Value: A 64-bit entity (or longer) that introduces randomness, enhancing security;
- Iteration Count: A numerical value dictating the number of hashing iterations, fortifying the encryption.
In an illustrative example, a Java implementation of password-based encryption might incorporate libraries and methodologies that meticulously adhere to the PKCS standard. Every nuance, from the derivation of keys to the encryption of data, is executed with precision, ensuring that the encrypted information is not only confidential but also securely authenticated.
Unraveling the Intricacies of Salt Value and Iteration Count
In the nuanced world of encryption, concepts like salt value and iteration count play a pivotal role in bolstering security. The salt value, a randomly generated set of keys, adds an extra layer of complexity to the encryption process. With a spectrum of possibilities, such as 2^128 keys for a 128-bit salt value, the encryption landscape becomes a maze, making unauthorized intrusion a Herculean task.
Similarly, the iteration count amplifies security by increasing the computational cost of key generation. With a baseline of 1000 iterations, the process can be tailored to meet specific security needs, ensuring that unauthorized decryption becomes a time-consuming and resource-intensive task.
Java’s SecretKeyFactory, paired with the “PBKDF2WithHmacSHA256” algorithm, stands as a sentinel, crafting keys with precision and security. The fusion of salt value and iteration count in this process underscores the robustness of Java’s encryption arsenal.
Exploring Java’s Cryptographic Libraries
Java’s cryptographic ecosystem is marked by its diversity and efficacy, offering tools and libraries that cater to varied encryption needs. In this expansive landscape, some libraries have distinguished themselves for their robustness and versatility:
- Bouncy Castle: Offers a plethora of cryptographic algorithms, providing developers a comprehensive toolkit for complex encryption tasks;
- Jasypt: Known for simplicity and ease of use, facilitates seamless integration with applications needing basic encryption functionalities;
- Apache Shiro: Marries simplicity with power, offering robust security features including encryption, authentication, and authorization.
These libraries contribute to Java’s repute as a flexible and powerful language for building secure applications. They encapsulate complexities, offering developers intuitive interfaces for implementing robust encryption.
AES Encryption Performance Optimization
Performance optimization in AES encryption is pivotal for enhancing efficiency and speed. Several strategies can be employed to optimize the encryption process:
- Algorithm Optimization: Utilizing optimized versions of algorithms to reduce computational load;
- Parallel Processing: Leveraging multi-core processors to execute encryption tasks in parallel, reducing processing time;
- Memory Management: Efficient management of memory resources to avoid bottlenecks during the encryption process.
Each strategy contributes to making AES encryption more efficient, ensuring that security doesn’t come at the expense of performance.
AES Key Management Best Practices
Key management stands as the cornerstone of effective AES encryption. It encompasses the creation, storage, distribution, and disposal of keys. Best practices in AES key management include:
- Regular Key Rotation: Periodically changing keys to mitigate the risk of unauthorized access;
- Secure Key Storage: Implementing secure storage mechanisms to safeguard keys from theft or loss;
- Access Control: Restricting access to keys, ensuring only authorized personnel can access them.
Adherence to these practices ensures that the integrity and confidentiality of encrypted data are maintained.
Conclusion
The multidimensional approach of AES in Java, characterized by its diverse modes and features, affirms its prominence in the realm of data encryption. It is a bastion of data security, offering a symphony of authenticity, integrity, and encryption that is tailor-made for varied data types and security requirements.
The nuanced integration of salt values and iteration counts, the versatility of cryptographic libraries, and the strategic optimization of performance underscore the holistic nature of Java’s encryption ecosystem. Every element, from key management practices to the intricate dance of encryption modes like GCM, CFB, and OFB, is orchestrated to create a fortress of security.
In the dynamic landscape of data security, AES in Java emerges as a harmonious blend of robustness, flexibility, and security. It is a testament to the language’s capability to evolve, adapt, and meet the complex, ever-changing demands of data encryption. Each mode, feature, and library is a chapter in this narrative of security, weaving a tapestry that safeguards data against the multifaceted threats of the digital age. The convergence of authenticity, integrity, and confidentiality in this ecosystem affirms Java’s position as an indispensable ally in the quest for unyielding data security.
No Comments
Sorry, the comment form is closed at this time.